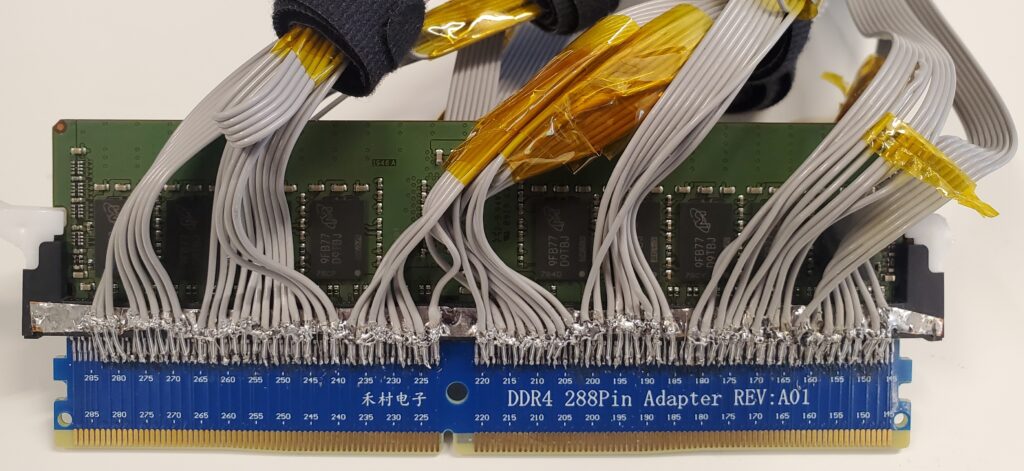
The important thing advantage of Battering RAM is that it requires tools that prices lower than $50 to tug off. It additionally permits lively decryption, that means encrypted information may be each learn and tampered with. As well as, it really works in opposition to each SGX and SEV-SNP, so long as they work with DDR4 reminiscence modules.
Wiretap
Wiretap, in the meantime, is proscribed to breaking solely SGX working with DDR4, though the researchers say it will probably work in opposition to the AMD protections with a modest quantity of extra work. Wiretap, nonetheless, permits just for passive decryption, which suggests protected information may be learn, however information can’t be written to protected areas of reminiscence. The price of the interposer and the tools for analyzing the captured information additionally prices significantly greater than Battering RAM, at about $500 to $1,000.
The Wiretap interposer.
Credit score:
Seto, et al.
The Wiretap interposer related to a logic analyzer.
Credit score:
Seto, et al.
Like Battering RAM, Wiretap exploits deterministic encryption, besides the latter assault maps ciphertext to an inventory of recognized plaintext phrases that the ciphertext is derived from. Finally, the assault can get better sufficient ciphertext to reconstruct the attestation key.
Genkin defined:
Let’s say you’ve an encrypted checklist of phrases that shall be later used to type sentences. You already know the checklist upfront, and also you get an encrypted checklist in the identical order (therefore the mapping between every phrase and its corresponding encryption). Then, if you encounter an encrypted sentence, you simply take the encryption of every phrase and match it in opposition to your checklist. By going phrase by phrase, you’ll be able to decrypt the whole sentence. In actual fact, so long as a lot of the phrases are in your checklist, you’ll be able to in all probability decrypt the whole dialog ultimately. In our case, we construct a dictionary between widespread values occurring inside the ECDSA algorithm and their corresponding encryption, after which use this dictionary to get better these values as they seem, permitting us to extract the important thing.
The Wiretap researchers went on to indicate the kinds of assaults which are potential when an adversary efficiently compromises SGX safety. As Intel explains, a key advantage of SGX is distant attestation, a course of that first verifies the authenticity and integrity of VMs or different software program working contained in the enclave and hasn’t been tampered with. As soon as the software program passes inspection, the enclave sends the distant social gathering a digitally signed certificates offering the identification of the examined software program and a clear invoice of well being certifying the software program is protected.